Getting Started with Wireshark
Introduction
Wireshark is a tool to analyze network traffic. Since KNX-IOT is all about IPV6 network traffic, wireshark can be used to analyze the network traffic of KNX-IOT.
Setup of Wireshark
Download and install wireshark from:
sniffing on PC (wired/wifi)
-
Start wireshark
This should now be an option in the start menu.
This should open the following start screen:
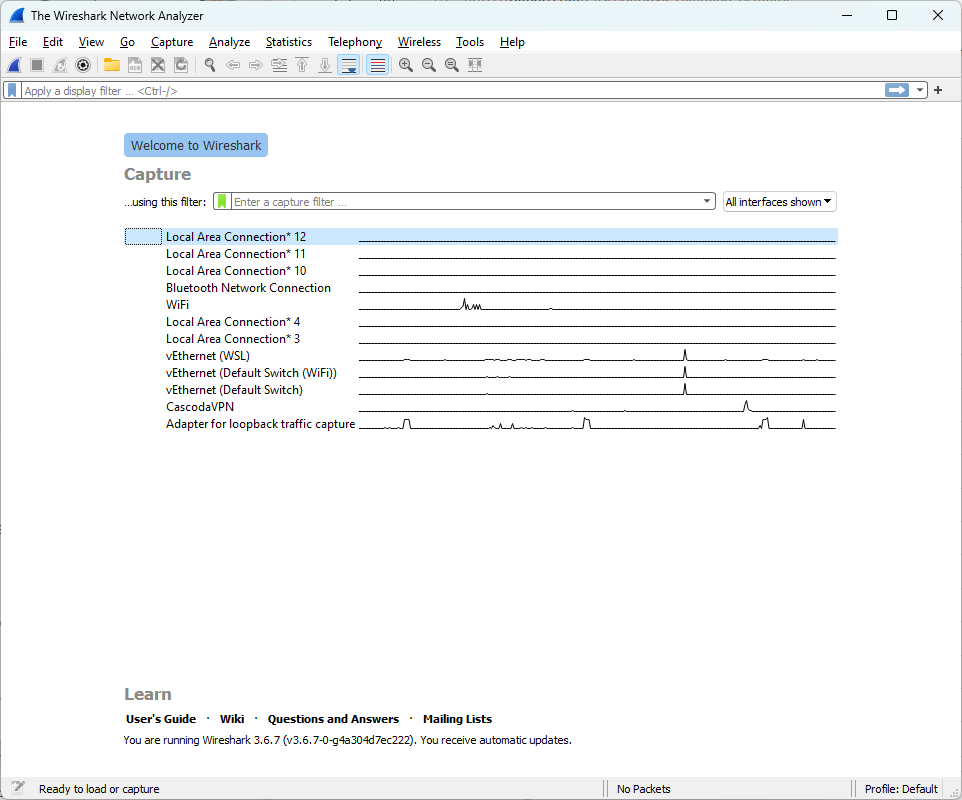 This shows the availble network interfaces.
For communication on the same pc select the loop back adapter.
This can be used when the virtual devices are running on the same PC.
This shows the availble network interfaces.
For communication on the same pc select the loop back adapter.
This can be used when the virtual devices are running on the same PC.Note: For capturing traffic between PC and other (physical) devices other interfaces needs to be selected, this depends on the PC and network configuration.
- The data is being captured.
- When enough data is captured one can stop capturing by pressing the
redbutton. -
To analyse the communication: select a packet with protocol
OSCORE. This is the security protocol used by KNX-IOT. To be able to see the encrypted data one should add the OSCORE security keys. This can be done via the popup menu structure below: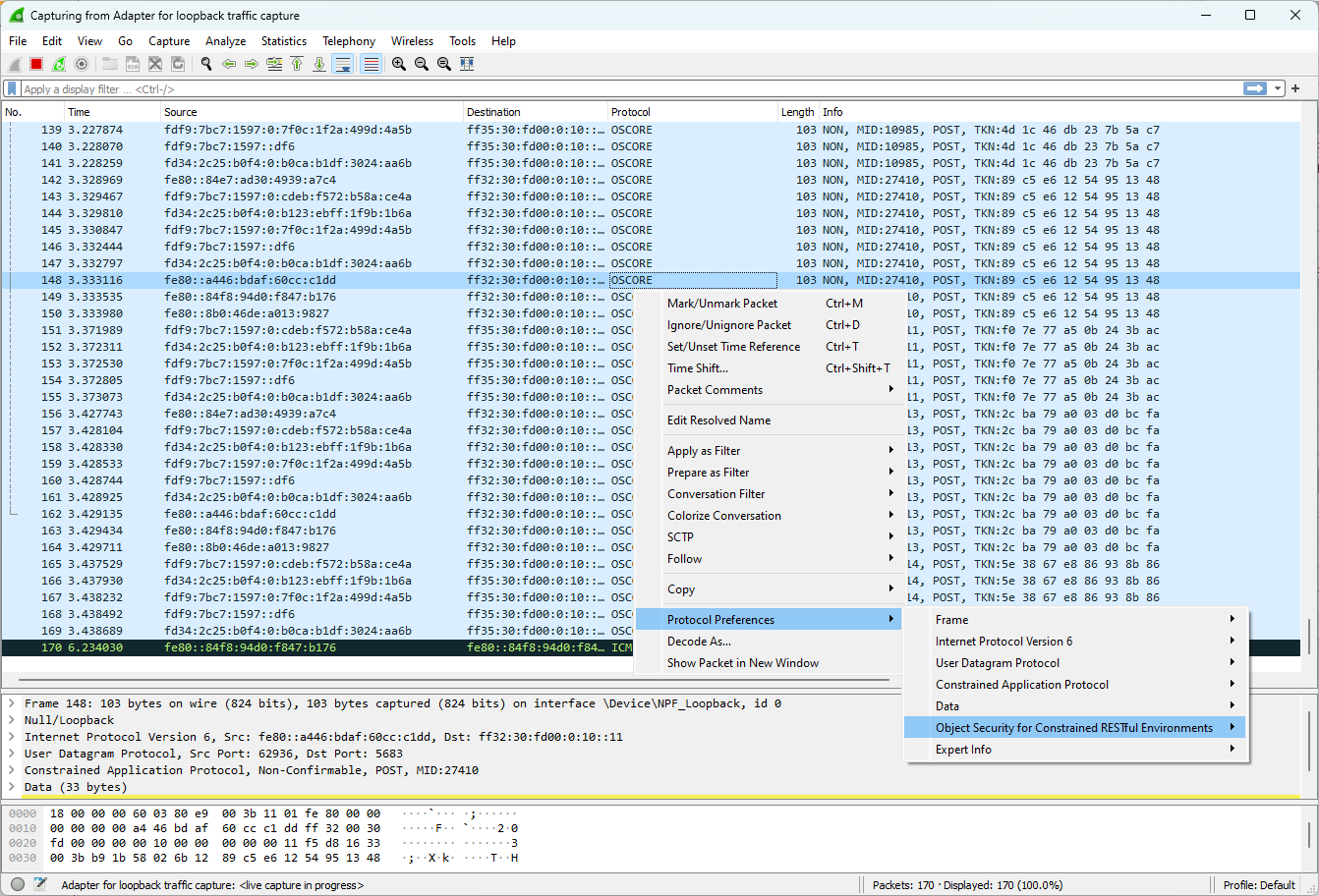
-
The security credentials needs to be entered in the
Security Contextpopup window.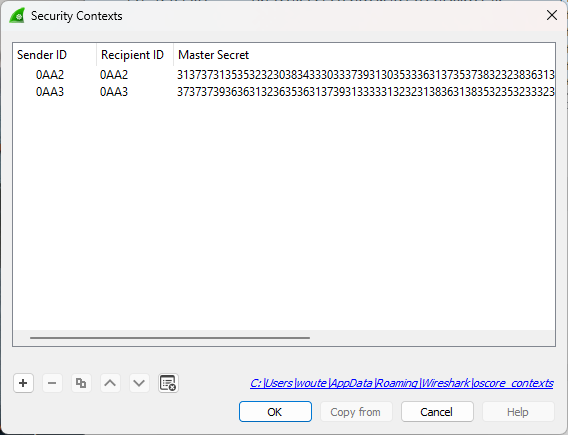 To add credentials press the
To add credentials press the +sign at the bottom of the window This action creates a new line and one can add the SenderID & Recipient id of the traffic (take the sender and recipient id from wireshark). The master secret needs to come from the application. -
When the credentials are entered then the stream can be decoded. The contents of the stream is visualized as a tree in the packet window. The tree can be expanded by pressing the tree sign (
>).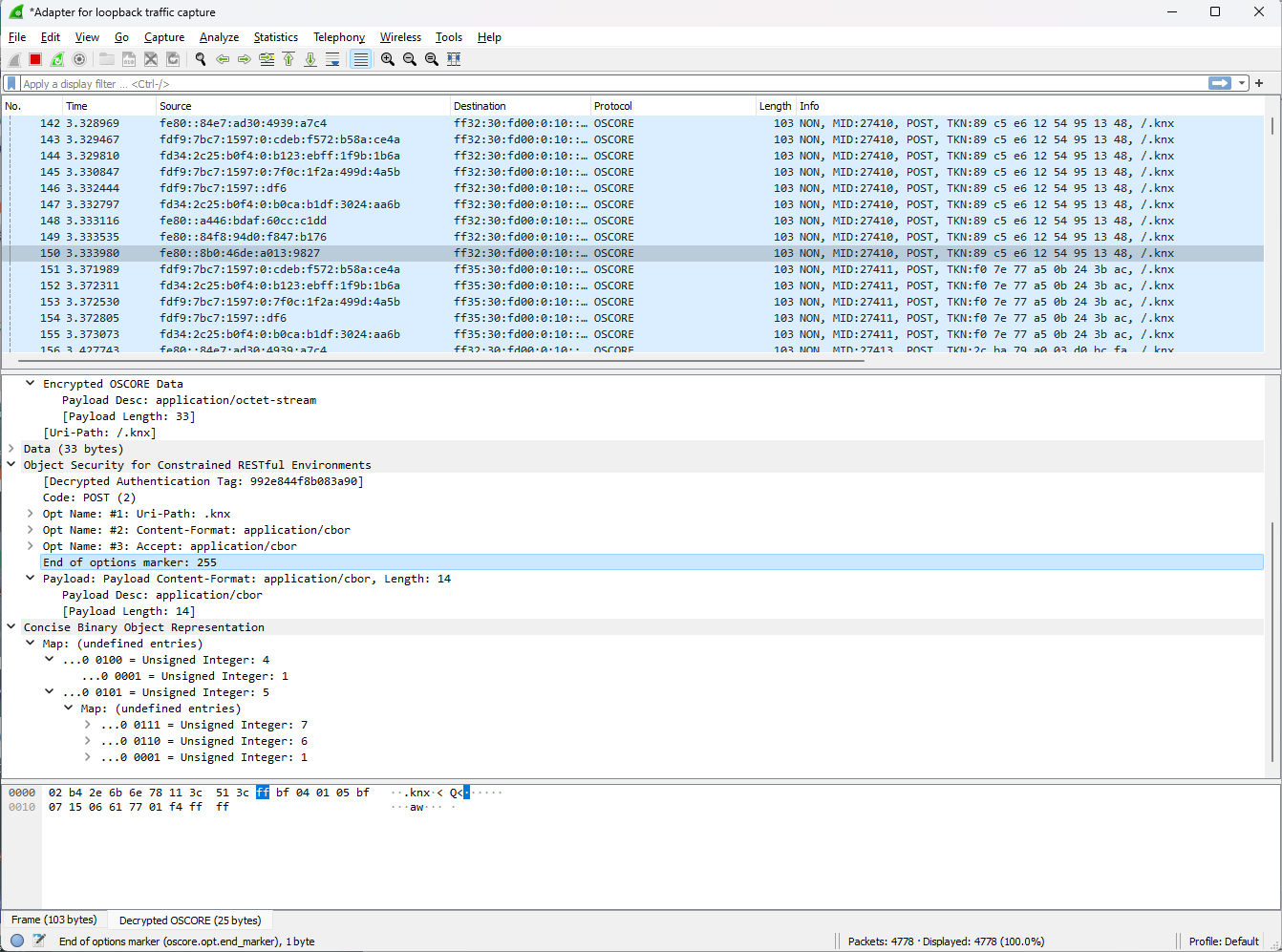 To make the OSCORE (decoded) payload visible one should press
To make the OSCORE (decoded) payload visible one should press Object Security for Constrained Restful Environments. Toe make the CBOR content visible one should press theConsise Binary Object Representation. The CBOR has different levels and can be expanded further. To understand CBOR, please take a look at cbor.me.If the credentials are not correctly entered, then the stream can’t be decrypted and message
[Expert Info (Warning/Undecoced): Security context not set - can't decrypt]is shown instead.
Sniffing on Thread)
Since Thread is a wireless protocol, one needs hardware to receive packets. This hardware is available: Thread sniffer](https://www.cascoda.com/products/packet-sniffer/)